
I recently shared the latest Cisco 300-440 exam practice questions with a 32-year-old IT engineer who was determined to earn his certification. In the 5 days leading up to the exam, he went through every single question thoroughly. These updated practice questions were the key to his success.
Here’s his story—and a reminder that you can do it too.
5-Day Challenge: Cisco 300-440 ENCC
He started out completely overwhelmed. Cloud architecture felt like a maze, and concepts like Infrastructure as Code (IaC) were intimidating. The 2025 version of the exam emphasized new trends such as Zero Trust security, and he worried he couldn’t keep up.
But then, he focused on the latest Cisco 300-440 ENCC practice questions—and that one decision changed everything.
Turning Point: Applying Cisco 300-440 ENCC Practice Questions in Real Scenarios
| Related | Exam Topics |
| CCNP Enterprise | 300-440 ENCC v1.0 |
Q1, Securing AWS Multi-Tier Applications
An engineer is implementing a highly securemultitierapplication in AWS that includes S3. RDS, and some additional private links. What is critical to keep the traffic safe?
A. VPC peering and bucket policies
B. specific routing and bucket policies
C. EC2 super policies and specific routing policies
D. gateway load balancers and specific routing policies
Correct Answer: B
A highly secure multitier application in AWS that includes S3, RDS, and some additional private links requires specific routing and bucket policies to keep the traffic safe. The reasons are as follows:
Specific routing policies are needed to ensure that the traffic between the tiers is routed through the private links, which provide secure and low-latency connectivity between AWS services and on-premises resources12. The private links can
also prevent the exposure of the data and the application logic to the public internet12. Bucket policies are needed to control the access to the S3 buckets that store the application data34. Bucket policies can specify the conditions under
which the requests are allowed or denied, such as the source IP address, the encryption status, the request time, etc.34. Bucket policies can also enforce encryption in transit and at rest for the data in S334.
References:
1: AWS PrivateLink
2: AWS PrivateLink FAQs
3: Using Bucket Policies and User Policies
4: Bucket Policy Examples
Q2: Internet-Based VPN Connectivity
Which architecture model establishes internet-based connectivity between on-premises networks and AWS cloud resources?
A. That establishes an iPsec VPN tunnel with Internet Key Exchange (IKE) for secure key negotiation and encrypted data transmission
B. That relies on AWS Elastic Load Balancing (ELB) for traffic distribution and uses SSL/TLS encryption for secure data transmission.
C. That employs AWS Direct Connect for a dedicated network connection and uses private IP addresses tor secure communication.
D. That uses Amazon CloudFrontfor caching and distributing content globally and uses HTTPS for secure data transfer.
Correct Answer: A
The architecture model that establishes internet-based connectivity between on-premises networks and AWS cloud resources is the one that establishes an iPsec VPN tunnel with Internet Key Exchange (IKE) for secure key negotiation and encrypted data transmission.
This model is also known as the VPN CloudHub model. It allows multiple remote sites to connect to the same virtual private gateway in AWS, creating a hub-and- spoke topology.
The VPN CloudHub model provides the following benefits: It enables secure communication between remote sites and AWS over the public internet, using encryption and authentication protocols such as IPsec and IKE.
It supports dynamic routing protocols such as BGP, which can automatically adjust the routing tables based on the availability and performance of the VPN tunnels.
It allows for redundancy and load balancing across multiple VPN tunnels, increasing the reliability and throughput of the connectivity.
It simplifies the management and configuration of the VPN connections, as each remote site only needs to establish one VPN tunnel to the virtual private gateway in AWS, rather than multiple tunnels to different VPCs or regions.
The other options are not correct because they do not establish internet-based connectivity between on-premises networks and AWS cloud resources.
Option B relies on AWS Elastic Load Balancing (ELB) for traffic distribution and uses SSL/TLS encryption for secure data transmission.
However, ELB is a service that distributes incoming traffic across multiple targets within a VPC, not across different networks.
Option C employs AWS Direct Connect for a dedicated network connection and uses private IP addresses for secure communication.
However, AWS Direct Connect is a service that establishes a private connection between on-premises networks and AWS, bypassing the public internet.
Option D uses Amazon CloudFront for caching and distributing content globally and uses HTTPS for secure data transfer. However, Amazon CloudFront is a service that delivers static and dynamic web content to end users, not to on-premises networks.
References:
1: Designing and Implementing Cloud Connectivity (ENCC, Track 1 of 5)
2: Cisco ASA Site-to-Site VPN
3: What Is Elastic Load Balancing?
4: What is AWS Direct Connect?
Q3: Fully Meshed SD-WAN Connectivity
A company with multiple branch offices wants a suitable connectivity model to meet these network architecture requirements:
1.
high availability
2.
quality of service (QoS)
3.
multihoming
4.
specific routing needs
Which connectivity model meets these requirements?
A. hub-and-spoke topology using MPLS with static routing and dedicated bandwidth for QoS
B. star topology with internet-based VPN connections and BGP for routing
C. hybrid topology that combines MPLS and SD-WAN
D. fully meshed topology with SD-WAN technology using dynamic routing and prioritized traffic for QoS
Correct Answer: D
A fully meshed topology with SD-WAN technology using dynamic routing and prioritized traffic for QoS meets the network architecture requirements of the company.
A fully meshed topology provides high availability by eliminating single points of failure and allowing multiple paths between branch offices.
SD-WAN technology enables multihoming by supporting multiple transport options, such as MPLS, internet, LTE, etc.
SD-WAN also provides QoS by applying policies to prioritize traffic based on application, user, or network conditions.
Dynamic routing allows the SD-WAN solution to adapt to changing network conditions and optimize the path selection for each traffic type.
A fully meshed topology with SDWAN technology can also support specific routing needs, such as segment routing, policy-based routing, or application-aware routing.
References:
Designing and Implementing Cloud Connectivity (ENCC) v1.0 [Cisco SD-WAN Design Guide]
[Cisco SD-WAN Configuration Guide]
Q4: Cisco SD-WAN Dynamic Path Selection
Which feature is unique to Cisco SD-WAN IPsec tunnels compared to native IPsec VPN tunnels?
A. real-time dynamic path selection
B. tunneling protocols
C. end-to-end encryption
D. authentication mechanisms
Correct Answer: A
Cisco SD-WAN IPsec tunnels are different from native IPsec VPN tunnels in several ways. One of the unique features of Cisco SD-WAN IPsec tunnels is that they support real-time dynamic path selection, which means that they can
automatically choose the best path for each application based on the network conditions and policies. This feature improves the performance, reliability, and efficiency of the network traffic. Native IPsec VPN tunnels, on the other hand, do not
have this capability and rely on static routing or manual configuration to select the path for each tunnel. This can result in suboptimal performance, increased latency, and higher costs.
References:
Traditional IPsec Versus Cisco SD-WAN IPsec, SD-WAN vs IPsec VPN\’s – What\’s the difference?, SD-WAN vs. VPN: How Do They Compare?, Traditional IPSEC Versus SD-WAN IPSEC
Q5: OMP Advertisement of BGP Routes in SD-WAN
An engineer must enable the OMP advertisement of BGP routes for a specific VRF instance on a Cisco IOS XE SD-WAN device. What should be configured after the global address-family ipv4 is configured?
A. Set the VRF-specific route advertisements.
B. Enable bgp advertisement.
C. Enter sdwan mode.
D. Disable bgp advertisement.
Correct Answer: B
To enable the OMP advertisement of BGP routes for a specific VRF instance on a Cisco IOS XE SD-WAN device, the engineer must first configure the global address-family ipv4 and then enable bgp advertisement under the vrf definition.
This will allow the device to advertise the BGP routes learned from the cloud provider to the OMP control plane, which will then distribute them to the other SD-WAN devices in the overlay network.
References:
Designing and Implementing Cloud Connectivity (ENCC) v1.0, Module 3:Implementing Cloud Connectivity, Lesson 3: Configuring IPsec VPN from Cisco IOS XE to AWS,
Topic: Configuring BGP on the Cisco IOS XE Device, Page 3-24.
Q6: Configuring Custom Applications in Cisco SD-WAN Centralized Policy
DRAG DROP
An engineer signs in to Cisco vManage and needs to configure a custom application with a Cisco SD-WAN centralized policy. Drag and drop the steps from the left onto the order on the right to complete the configuration.
Select and Place:
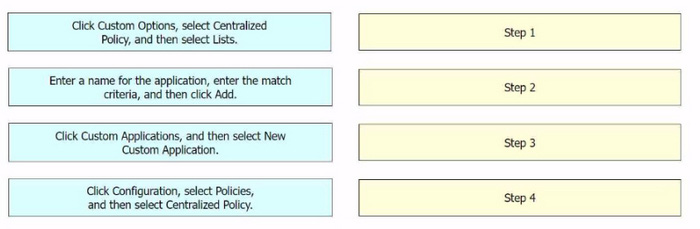
Correct Answer:
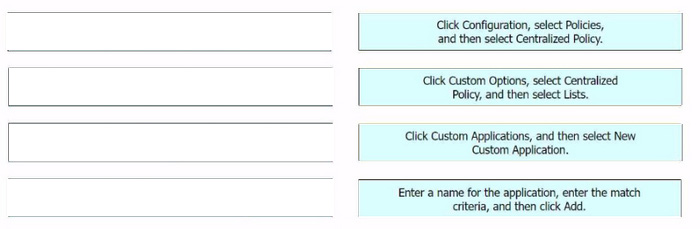
The process of configuring a custom application with a Cisco SD-WAN centralized policy using Cisco vManage involves several steps.
Click Configuration, select Policies, and then select Centralized Policy: This is the first step where you navigate to the Policies section in the Configuration menu of Cisco vManage.
Click Custom Options, select Centralized Policy, and then select Lists: In this step, you select the Custom Options, then select Centralized Policy, and finally select Lists.
Click Custom Applications, and then select New Custom Application: After setting up the Lists, you click on Custom Applications and then select New Custom Application.
Enter a name for the application, enter the match criteria, and then click Add:
Finally, you enter a name for the application, specify the match criteria, and then click Add to complete the configuration.
References:
Cisco Catalyst SD-WAN Policies Configuration Guide, Cisco IOS XE
Q7: Configuring SLA Class in Cisco vManage
DRAG DROP
An engineer must use Cisco vManage to configure an SLA class to specify the maximum packet loss, packet latency, and jitter allowed on a connection. Drag and drop the steps from the left onto the order on the right to complete the configuration.
Select and Place:
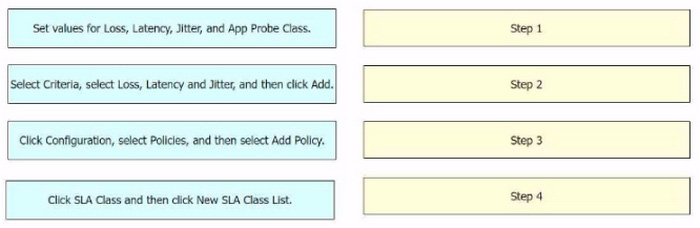
Correct Answer:
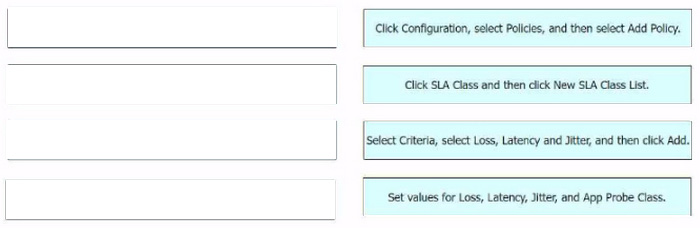
The process of configuring an SLA class to specify the maximum packet loss, packet latency, and jitter allowed on a connection using Cisco vManage involves several steps. Click Configuration, select Policies, and then select Add Policy:
This is the first step where you navigate to the Policies section in the Configuration menu of Cisco vManage.
Click SLA Class and then click New SLA Class List: In this step, you create a new SLA Class List.
Select Criteria, select Loss, Latency and Jitter, and then click Add: After setting up the SLA Class List, you select the criteria for the SLA class. In this case, the criteria are Loss, Latency, and Jitter.
Set values for Loss, Latency, Jitter, and App Probe Class: Finally, you set the values for Loss, Latency, Jitter, and App Probe Class.
References:
Information About Application-Aware Routing – Cisco Policies Configuration Guide for vEdge Routers, Cisco SD-WAN Release
Q8: Fully Meshed SD-WAN with BGP Routing
A company with multiple branch offices wants a connectivity model to meet its network architecture requirements. The company focuses on ensuring low latency and efficient routing for its critical business applications. Which connectivity model meets these requirements?
A. hub-and-spoke topology with SD-WAN technology, using dynamic routing and OSPF as the routing protocol
B. fully meshed topology with SD-WAN technology, using dynamic routing and BGP as the routing protocol
C. point-to-point topology using dedicated leased lines and static routing
D. star topology with internet-based VPN connections and static routing
Correct Answer: B
A fully meshed topology with SD-WAN technology, using dynamic routing and BGP as the routing protocol, meets the requirements of the company because it provides the following benefits
It allows direct and secure connectivity between any two branch offices, without the need for a central hub or intermediary devices.
This reduces the latency and improves the performance of the critical business applications. It leverages SDWAN technology to optimize the traffic flow and application quality of service (QoS) across the WAN.
SD-WAN can dynamically select the best path for each application based on the network conditions and policies.
SD- WAN can also provide redundancy, security, and visibility for the WAN. It uses dynamic routing and BGP as the routing protocol to exchange routing information and establish connectivity between the branch offices.
BGP is a scalable and flexible protocol that can support multiple address families, such as IPv4 and IPv6, and multiple routing policies, such as local preference and route filtering.
BGP can also enable seamless integration with the cloud service providers (CSPs) and internet service providers (ISPs).
References :
1: Designing and Implementing Cloud Connectivity (ENCC, Track 1 of 5) (Cisco U.login required)
2: Cisco SD-WAN Design Guide
Q9: Configuring IPsec Tunnel Traffic Routing
An engineer must configure an IPsec tunnel to the cloud VPN gateway. Which Two actions send traffic into the tunnel? (Choose two.)
A. Configure access lists that match the interesting user traffic.
B. Configure a static route.
C. Configure a local policy in Cisco vManage.
D. Configure an IPsec profile and match the remote peer IP address.
E. Configure policy-based routing.
Correct Answer: AE
To send traffic into an IPsec tunnel to the cloud VPN gateway, the engineer must configure two actions:
Configure access lists that match the interesting user traffic. This is the traffic that needs to be encrypted and sent over the IPsec tunnel. The access lists are applied to the crypto map that defines the IPsec parameters for the tunnel.
Configure policy-based routing (PBR). This is a technique that allows the engineer to override the routing table and forward packets based on a defined policy.
PBR can be used to send specific traffic to the IPsec tunnel interface, regardless of the destination IP address. This is useful when the cloud VPN gateway has a dynamic IP address or when multiple cloud VPN gateways are available for load balancing or redundancy.
References:
Designing and Implementing Cloud Connectivity (ENCC) v1.0, Module 3:
Implementing Cloud Connectivity, Lesson 3: Implementing IPsec VPNs to the Cloud, Topic: Configuring IPsec VPNs on Cisco IOS XE Routers Security for VPNs with IPsec Configuration Guide, Cisco IOS XE, Chapter:
Configuring IPsec VPNs, Topic: Configuring Crypto Maps [Cisco IOS XE Gibraltar 16.12.x Feature Guide], Chapter: Policy-Based Routing, Topic: Policy-Based Routing Overview
Q10: Configuring IPsec VPN Tunnel Source
Refer to the exhibit.
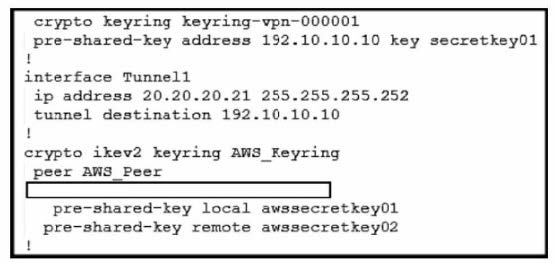
An engineer needs to configure a site-to-site IPsec VPN connection between an on-premises Cisco IOS XE router and Amazon Web Services (AWS). Which configuration command must be placed in the blank in the code to complete the tunnel configuration?
A. address 20.20.20.21
B. address 192.10.10.10
C. tunnel source 20.20.20.21
D. tunnel source 192.10.10.10
Correct Answer: C
In the given scenario, an engineer is configuring a site-to-site IPsec VPN connection between an on-premises Cisco IOS XE router and AWS.
The correct command to complete the tunnel configuration is “tunnel source 20.20.20.21”. This command specifies the source IP address for the tunnel, which is essential for establishing a secure connection between two endpoints over the internet or another network.
References: Configure IOS-XE Site-to-Site VPN Connection to Amazon Web Services – Cisco Community [Security for VPNs with IPsec Configuration Guide, Cisco IOS XE Release 3S – Config
Q11: Centralized Internet Gateway for SaaS Connectivity
Which approach does a centralized internet gateway use to provide connectivity to SaaS applications?
A. A cloud-based proxy server routes traffic from the on-premises infrastructure to the SaaS provider data center.
B. Internet traffic from the on-premises infrastructure is routed through a centralized gateway that provides access controls for SaaS applications.
C. VPN connections are used to provide secure access to SaaS applications from the on- premises infrastructure.
D. A dedicated, private connection is established between the on-premises infrastructure and the SaaS provider data center using colocation services.
Correct Answer: B
A centralized internet gateway is a network design that routes all internet- bound traffic from the on-premises infrastructure through a single point of egress, typically located at the data center or a regional hub1.
This approach allows the enterprise to apply consistent security policies and access controls for SaaS applications, as well as optimize the bandwidth utilization and performance of the WAN links.
A centralized internet gateway can use various technologies to provide connectivity to SaaS applications, such as proxy servers, firewalls, web filters, and WAN optimizers.
However, a cloud-based proxy server (option A) is not a part of the centralized internet gateway, but rather a separate service that can be used to route traffic from the on-premises infrastructure to the SaaS provider data center4.
VPN connections (option C) and dedicated, private connections (option D) are also not related to the centralized internet gateway, but rather alternative ways of providing secure and reliable access to SaaS applications from the on- premises infrastructure5.
Therefore, the correct answer is option B, which describes the basic function of a centralized internet gateway.
Q12: Configuring Cisco Umbrella SIG Active/Backup Mode
DRAG DROP
An engineer must configure cloud connectivity with Cisco Umbrella Secure Internet Gateway (SIG) in active/backup mode. The engineer already configured the SIG Credentials and SIG Feature Templates. Drag and drop the steps from the left onto the order on the right to complete the configuration.
Select and Place:
Correct Answer:
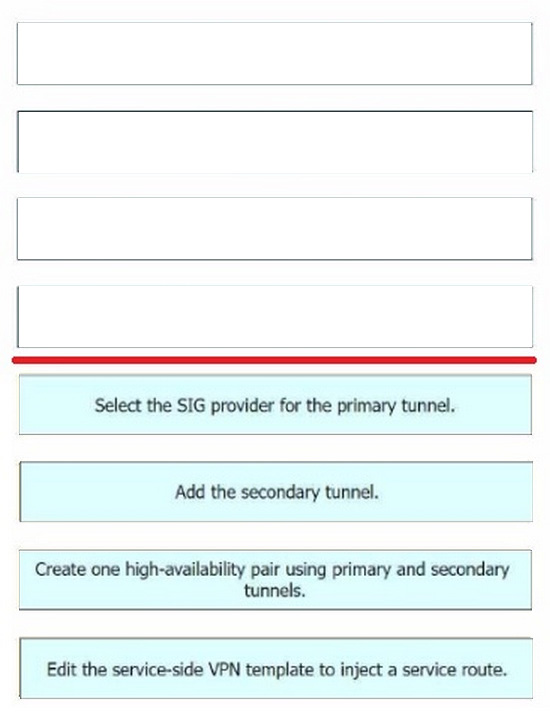
The configuration of cloud connectivity with Cisco Umbrella Secure Internet Gateway (SIG) in active/backup mode involves several steps.
After configuring the SIG Credentials and SIG Feature Templates, the engineer must: Select the SIG provider for the primary tunnel: This is the first step in setting up the active/backup mode. The primary tunnel is the main connection path for the cloud connectivity.
Add the secondary tunnel: The secondary tunnel serves as a backup in case the primary tunnel fails. It ensures that the cloud connectivity remains uninterrupted even if there are issues with the primary tunnel.
Create one high-availability pair using primary and secondary tunnels: This step involves pairing the primary and secondary tunnels to create a high-availability pair.
Thisensures that the cloud connectivity will switch over to the secondary tunnel seamlessly if the primary tunnel fails. Edit the service-side VPN template to inject a service route: The final step involves modifying the VPN template on the service side to include a service route.
This ensures that the traffic is correctly routed through the primary or secondary tunnel as needed.
References:
Designing and Implementing Cloud Connectivity (ENCC) v1.01 Learning Plan: Designing and Implementing Cloud Connectivity v1.0 (ENCC 300- 440) Exam Prep2 Configure Umbrella SIG Tunnels for Active/Backup or Active/Active Scenarios – Cisco
Q13: Configuring Cisco SD-WAN Cloud Interconnect with Equinix
DRAG DROP
Refer to the exhibit.
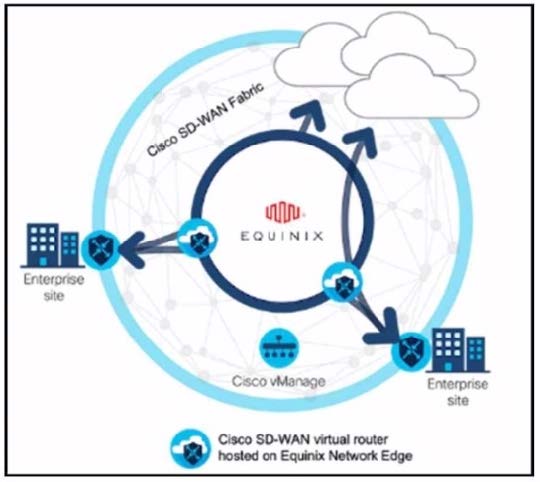
These configurations are complete:
1.
Create an account in the Equinix portal.
2.
Associate the Equinix account with Cisco vManage.
3.
Configure the global settings for Interconnect Gateways.
Drag the prerequisite steps from the left onto the order on the right to configure a Cisco SD-WAN Cloud Interconnect with Equinix
Select and Place:
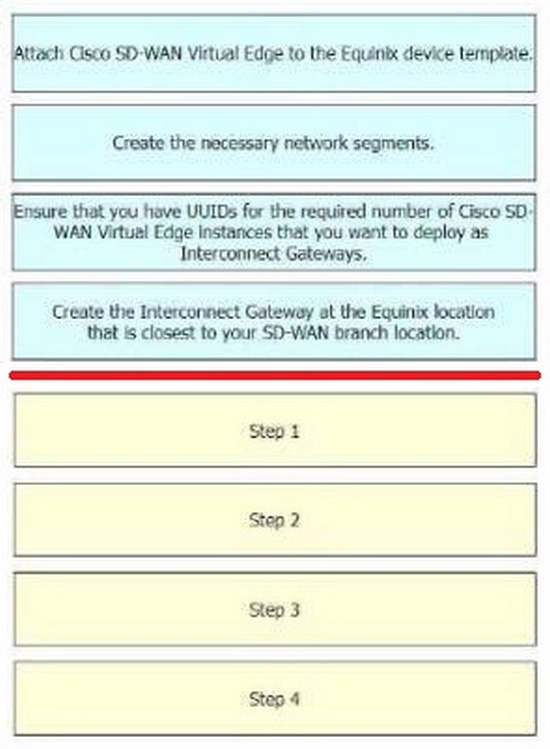
Correct Answer:
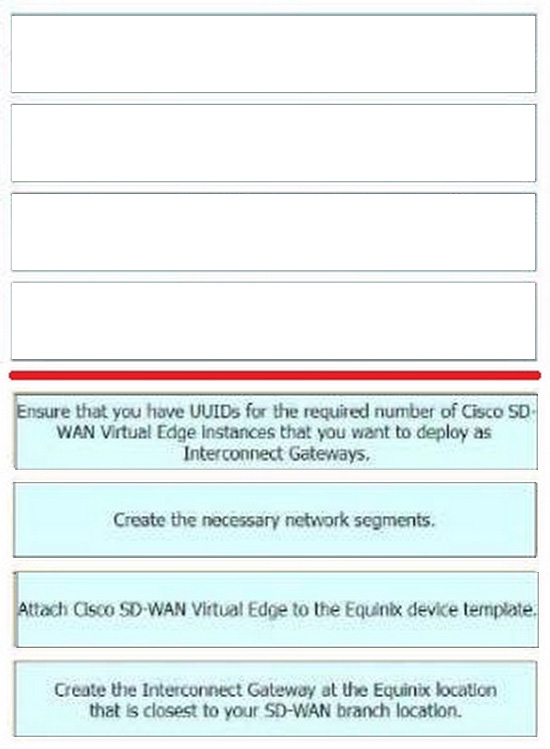
The process of configuring a Cisco SD-WAN Cloud Interconnect with Equinix involves several steps.
Ensure that you have UUIDs for the required number of Cisco SD WAN Virtual Edge instances that you want to deploy as Interconnect Gateways: This is the first step where you ensure that you have the necessary UUIDs for the Cisco SDWAN Virtual Edge instances that you want to deploy.
Create the necessary network segments: After ensuring the availability of UUIDs, you create the necessary network segments.
Attach Cisco SD-WAN Virtual Edge to the Equinix device template: After setting up the network segments, you attach the Cisco SD-WAN Virtual Edge to the Equinix device template.
Create the Interconnect Gateway at the Equinix location that is closest to your SD- WAN branch location: Finally, you create the Interconnect Gateway at the Equinix location that is closest to your SD-WAN branch location.
References:
[Cisco SD-WAN Cloud Interconnect with Equinix]
[Cisco SD-WAN Cloud OnRamp for CoLocation Deployment Guide]
Q14: Troubleshooting Cisco IOS XE SD-WAN Issues
DRAG DROP
Drag and drop the commands from the left onto the purposes on the right to identify issues on a Cisco IOS XE SD-WAN device.
Select and Place:
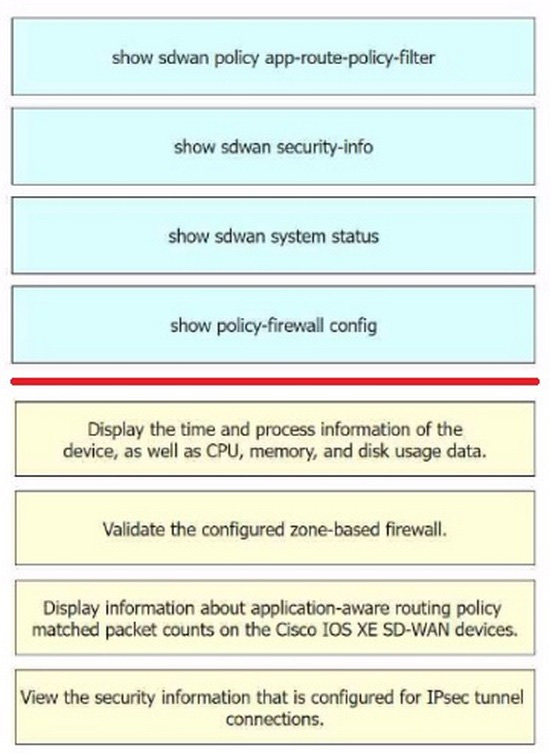
Correct Answer:

Display the time and process information of the device, as well as CPU, memory, and disk usage data.
= show sdwan system status Validate the configured zone-based firewall.
= show policy-firewall config1 Display information about application-aware routing policy matched packet counts on the Cisco IOS XE SD-WAN devices.
= show sdwan policy app-route-policy- filter View the security information that is configured for IPsec tunnel connections.
= show sdwan security-info The commands used to identify issues on a Cisco IOS XE SD-WAN device are as follows show sdwan system status:
This command is used to display the time and process information of the device, as well as CPU, memory, and disk usage data.
show policy-firewall config:
This command is used to validate the configured zone-based firewall.
show sdwan policy app-route-policy-filter:
This command is used to display information about application-aware routing policy matched packet counts on the Cisco IOS XE SD-WAN devices.
show sdwan security-info: This command is used to view the security information that is configured for IPsec tunnel connections
References: Cisco IOS XE Catalyst SD-WAN Qualified Command Reference Cisco Catalyst SD-WAN Command Reference Cisco Catalyst SD-WAN Systems and Interfaces Configuration Guide, Cisco IOS XE SD-WAN Tunnel Interface Commands – Cisco
Q15: Cisco SD-WAN Policy Configuration
Refer to the exhibit.
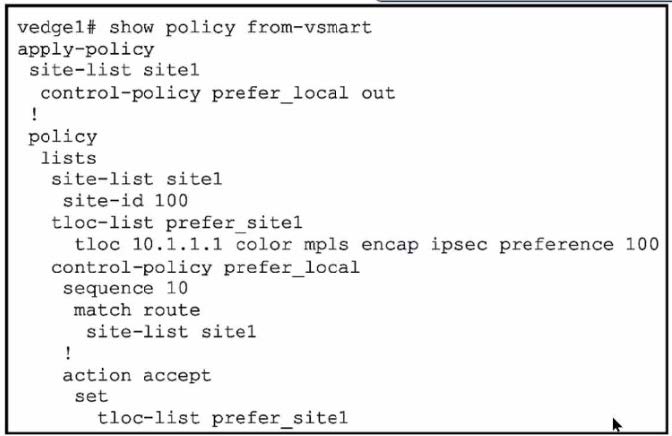
A network engineer discovers that the policy that is configured on an on-premises Cisco WAN edge router affects only the route tables of the specific devices that are listed in the site list. What is the problem?
A. An inbound policy must be applied.
B. The action must be set to deny
C. A localized data policy must be configured.
D. A centralized data policy must be configured
Correct Answer: D
A centralized data policy is a policy that is applied to all devices in the overlay network, regardless of the site list. A localized data policy is a policy that is applied only to the devices that are listed in the site list.
In this case, the network engineer wants to apply the policy to all devices in the overlay network, not just the specific devices in the site list.
Therefore, a centralized data policy must be configured on the on-premises Cisco WAN edge router.
References:
Designing and Implementing Cloud Connectivity (ENCC) v1.0, Module 3:
Implementing Cloud Connectivity, Lesson 3: Implementing Cisco SD-WAN Cloud OnRamp for Colocation, Topic: Centralized Data Policy [Cisco SD-WAN Cloud OnRamp for Colocation Deployment Guide], Chapter:
Configuring Centralized Data Policy
Her Understanding Summary
The above demonstrates part of his acquired knowledge: understanding cloud connectivity concepts such as Internet-Based VPN Connectivity, Fully Meshed SD-WAN with BGP Routing, and Cisco SD-WAN Dynamic Path Selection, enabling him to design efficient and secure network architectures.
In the realm of automation, he learned to configure SLA classes in Cisco vManage and the OMP advertisement of BGP routes in SD-WAN, enhancing his ability to optimize network workflows. In terms of security, he mastered configuring IPsec VPN tunnel sources, Centralized Internet Gateway for SaaS connectivity, and Cisco Umbrella SIG Active/Backup Mode, strengthening his capacity to protect cloud environments.
Cisco 300-440 ENCC Success Strategy
Practice 10 questions a day and simulate the exam environment under timed conditions. Review mistakes using official Cisco documentation, and seek advice in forums when needed. Make sure to consistently score 90% on mock exams.
Leave one day for rest—on exam day, the familiar questions helped him pass with ease.
You Can Succeed Too: Cisco 300-440 ENCC
Five days may not seem like much, but with the right strategy—especially the latest practice questions—you can make passing the Cisco 300-440 ENCC exam a reality in the shortest time possible.
Start practicing with targeted questions and review your mistakes carefully.
Get the latest Cisco 300-440 ENCC practice questions here: https://www.leads4pass.com/300-440.html and kick off your exam journey today!