
The Cisco Certified CyberOps Associate (CBROPS 200-201) certification is one of the most recognized entry-level credentials in the cybersecurity operations field. It validates your ability to detect, analyze, and respond to cybersecurity threats in a modern Security Operations Center (SOC) environment.
If you are planning to take the Latest version of the exam, we strongly recommend starting with the Leads4Pass CBROPS 200-201 Practice Exam (https://www.leads4pass.com/200-201.html), which offers updated, verified questions aligned with Cisco’s latest official exam blueprint.
Official CBROPS 200-201 Exam Overview
According to Cisco’s official exam page, the CBROPS 200-201 exam is required to earn the Cisco Certified CyberOps Associate certification.
- Exam Name: Understanding Cisco Cybersecurity Operations Fundamentals
- Exam Code: 200-201 CBROPS
- Duration: 120 minutes
- Question Types: Multiple-choice, drag-and-drop, scenario-based questions
- Language: English
- Validity: 3 years
This certification validates foundational cybersecurity skills used by analysts and engineers in real-world SOC environments.
CBROPS 200-201 Exam Domains and Topic Weight
| Domain | Weight | Core Focus |
|---|---|---|
| Security Concepts | 20% | CIA triad, risk management, access control models |
| Security Monitoring | 25% | SIEM operations, event classification, log correlation |
| Host-Based Analysis | 20% | File forensics, malware detection, system processes |
| Network Intrusion Analysis | 20% | IDS/IPS mechanisms, PCAP packet analysis |
| Security Policies & Procedures | 15% | Incident response, compliance, data privacy |
Key takeaway: Focus heavily on Security Monitoring and Network Intrusion Analysis since Cisco’s recent updates emphasize these two areas.
The 12-Week 200-201 CBROPS Study Plan
Phase 1 – Build the Foundation (Weeks 1–4)
- Study networking fundamentals and security basics.
- Read CBROPS Official Cert Guide by Cisco Press.
- Watch Cisco’s official NetAcad CBROPS course videos.
- Use Wireshark to analyze real traffic and understand packet flows.
Phase 2 – Deep Dive per Domain (Weeks 5–8)
- Week 5: Focus on Security Monitoring (SIEM & log analysis).
- Week 6: Master Host-Based Analysis (Windows & Linux artifacts).
- Week 7: Learn Network Intrusion Analysis using PCAPs.
- Week 8: Review Security Policies & Procedures.
Phase 3 – Practice and Mock Testing (Weeks 9–12)
- Take full-length mock exams on Leads4Pass 200-201 Practice Tests (https://www.leads4pass.com/200-201.html).
- Review incorrect answers and re-learn weak areas.
- Simulate real-time SOC analysis and response scenarios.
Recommended Cisco Tools and Platforms
| Tool / Platform | Purpose | Link |
|---|---|---|
| Cisco NetAcad | Official CBROPS online course | NetAcad |
| Cisco Modeling Labs (CML) | Lab simulation environment | Cisco Official |
| Splunk Free Edition | SIEM log monitoring practice | Splunk.com |
| Wireshark | Network packet analysis | Wireshark.org |
| Leads4Pass CBROPS Practice Tests | Updated question sets | Visit Here |
Common Mistakes and How to Avoid Them
| Mistake | How to Fix It |
|---|---|
| Memorizing questions instead of understanding | Focus on “why” behind each answer |
| Ignoring hands-on experience | Practice with Splunk or Wireshark weekly |
| Poor time management | Study 90 minutes daily + weekend review |
| Not tracking Cisco updates | Follow Cisco Learning Blog regularly |
Latest CBROPS 200-201 Practice Question & Answer
| Number of exam questions | Complete exam materials |
| 15 (Free) | 491 Q&A |
Question 1:
According to the September 2020 threat intelligence feeds a new malware called Egregor was introduced and used in many attacks. Distnbution of Egregor is pnmanly through a Cobalt Strike that has been installed on victim\’s workstations using RDP exploits Malware exfiltrates the victim\’s data to a command and control server. The data is used to force victims pay or lose it by publicly releasing it. Which type of attack is described?
A. malware attack
B. ransomware attack
C. whale-phishing
D. insider threat
Correct Answer: B
Question 2:
A cyberattacker notices a security flaw in a software that a company is using. They decide to tailor a specific worm to exploit this flaw and extract saved passwords from the software. To which category of the Cyber Kill Chain model does this event belong?
A. weaponization
B. reconnaissance
C. delivery
D. exploitation
Correct Answer: A
Question 3:
What is the difference between the ACK flag and the RST flag?
A. The ACK flag validates the next packets to be sent to a destination, and the RST flag is what the RST returns to indicate that the destination is reachable.
B. The RST flag establishes the communication, and the ACK flag cancels spontaneous connections that were not specifically sent to the expecting host.
C. The RST flag identifies the connection as reliable and trustworthy within the handshake process, and the ACK flag prepares a response by opening a session between the source and destination.
D. The ACK flag validates the receipt of the previous packet in the stream, and the same session is being closed by the RST flag.
Correct Answer: D
Question 4:
What is the practice of giving an employee access to only the resources needed to accomplish their job?
A. principle of least privilege
B. organizational separation
C. separation of duties
D. need to know principle
Correct Answer: A
Question 5:
Refer to the exhibit.

Which type of log is displayed?
A. IDS
B. proxy
C. NetFlow
D. sys
Correct Answer: A
Explanation:
You also see the 5-tuple in IPS events, NetFlow records, and other event data. In fact, on the exam you may need to differentiate between a firewall log versus a traditional IPS or IDS event. One of the things to remember is that traditional IDS and IPS use signatures, so an easy way to differentiate is by looking for a signature ID (SigID). If you see a signature ID, then most definitely the event is a traditional IPS or IDS event.
Question 6:
Refer to the exhibit.
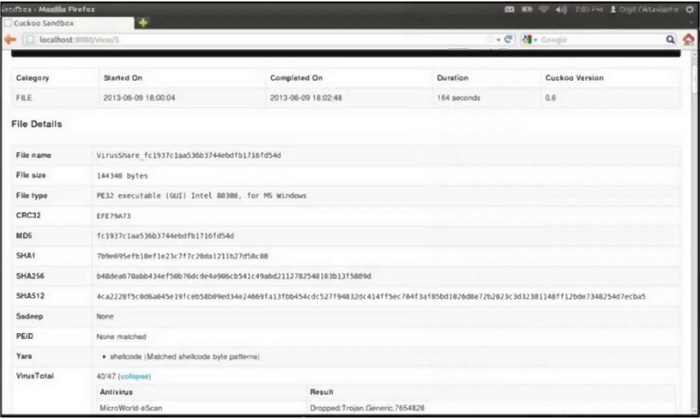
What does this Cuckoo sandbox report indicate?
A. The file is ransomware.
B. The file is spyware.
C. The file will open unsecure ports when executed.
D. The file will open a command interpreter when executed.
Correct Answer: B
Question 7:
Refer to the exhibit.
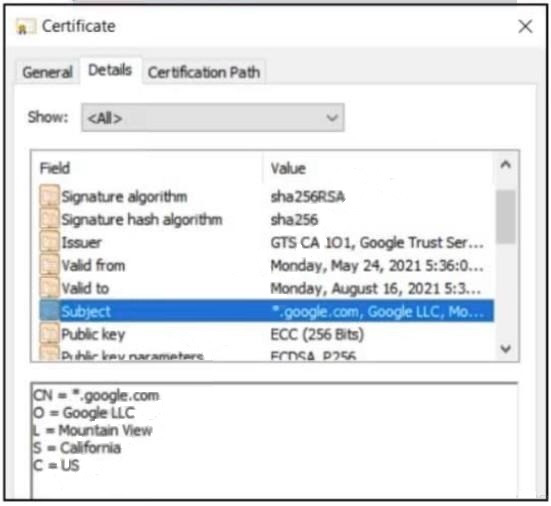
An engineer needs to identify certificate information on server1234567890. What does the exhibit indicate?
A. Elliptic-curve cryptography is used for the public keys.
B. Key exchange is not secure as the SHA256 hashing algorithm is used.
C. The certificate is signed by GTS CA on May 24 and is invalid.
D. Asymmetric cryptography is used for key exchange.
Correct Answer: A
Question 8:
Refer to the exhibit.
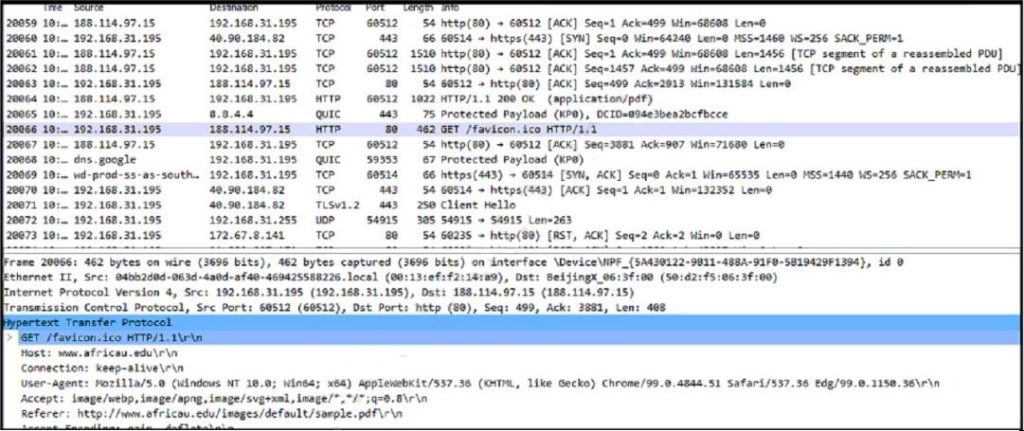
Which frame numbers contain a file that is extractable from Wireshark PCAP?
A. Frames No. 20064 and 20066
B. Frame No. 20064
C. Frame No. 20086
D. All Frames from No. 20061 to 20064
Correct Answer: D
Explanation:
D. All Frames from No. 20061 to 20064
Here\’s why:
Frame 20061: This frame shows the beginning of a TCP reassembled PDU (Packet Data Unit) with a length of 60512 bytes. This suggests that a file transfer is starting.
Frame 20062: This frame continues the reassembled PDU, indicating that the file transfer is ongoing.
Frame 20063: This frame shows the end of the reassembled PDU with a “TCP segment of a reassembled PDU” label, confirming that the file transfer is complete.
Frame 20064: This frame shows a 75-byte payload identified as “Protected Payload (KPO), DCID-094e3bea2bcfbcce”. This suggests that the extracted file might be encrypted or obfuscated in some way.
Frames 20065 and 20066 show subsequent traffic related to HTTP and QUIC protocols, but not directly related to the file transfer initiated in frame 20061.
Therefore, all frames from 20061 to 20064, including the reassembled PDU and the protected payload, are likely to contain the extractable file.
Question 9:
Which type of attack involves executing arbitrary commands on the operating system to escalate privileges?
A. Apache log
B. cross-site scripting
C. command injection
D. SQL injection
Correct Answer: C
Question 10:
According to CVSS, what is a description of the attack vector score?
A. It depends on how far away the attacker is located and the vulnerable component.
B. The metric score will be larger when a remote attack is more likely.
C. It depends on how many physical and logical manipulations are possible on a vulnerable component.
D. The metric score will be larger when it is easier to physically touch or manipulate the vulnerable component.
Correct Answer: B
Question 11:
What describes the usage of a rootkit in endpoint-based attacks?
A. remote code execution that causes a denial-of-service on the system
B. exploit that can be used to perform remote code execution
C. set of vulnerabilities used by an attacker to disable root access on the system
D. set of tools used by an attacker to maintain control of a compromised system while avoiding detection
Correct Answer: D
Question 12:
Refer to the exhibit.

Which event is occurring?
A. A binary named “submit” is running on VM cuckoo1.
B. A binary is being submitted to run on VM cuckoo1
C. A binary on VM cuckoo1 is being submitted for evaluation
D. A URL is being evaluated to see if it has a malicious binary
Correct Answer: B
https://cuckoo.readthedocs.io/en/latest/usage/submit
Question 13:
How does rule-based detection differ from behavioral detection?
A. Rule-based systems have predefined patterns, and behavioral systems learn the patterns that are specific to the environment.
B. Rule-based systems search for patterns linked to specific types of attacks, and behavioral systems identify attacks per signature.
C. Behavioral systems have patterns are for complex environments, and rule-based systems can be used on low-mid-sized businesses.
D. Behavioral systems find sequences that match particular attack behaviors, and rule-based systems identify potential zero-day attacks.
Correct Answer: A
Question 14:
A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the same data center were transferred to a competitor. Which type of evidence is this?
A. best evidence
B. prima facie evidence
C. indirect evidence
D. physical evidence
Correct Answer: C
Explanation:
There are three general types of evidence:
–> Best evidence: can be presented in court in the original form (for example, an exact copy of a hard disk drive).
–> Corroborating evidence: tends to support a theory or an assumption deduced by some initial evidence. This corroborating evidence confirms the proposition. –> Indirect or circumstantial evidence: extrapolation to a conclusion of fact (such
as fingerprints, DNA evidence, and so on).
Question 15:
What is the difference between statistical detection and rule-based detection models?
A. Rule-based detection involves the collection of data in relation to the behavior of legitimate users over a period of time
B. Statistical detection defines legitimate data of users over a period of time and rule-based detection defines it on an IF/THEN basis
C. Statistical detection involves the evaluation of an object on its intended actions before it executes that behavior
D. Rule-based detection defines legitimate data of users over a period of time and statistical detection defines it on an IF/THEN basis
Correct Answer: B
…
Career Benefits and Salary Outlook
With the growing global demand for SOC professionals, CBROPS 200-201 certification holders can pursue roles such as:
- Security Operations Analyst
- Incident Responder
- Threat Intelligence Analyst
According to PayScale 2025, the average annual salary for CBROPS-certified professionals ranges between $85,000–$105,000 in the U.S.
CBROPS 200-201 Updates and Emerging Topics
Cisco’s 2025 CBROPS blueprint includes expanded coverage on:
- Cloud Security Monitoring (AWS, Azure, GCP logs)
- AI-Driven Threat Detection (machine learning-based SOC operations)
- Security Automation (SOAR) and Cisco XDR integration
Cisco encourages candidates to familiarize themselves with SecureX, Talos Intelligence, and Cisco XDR platforms as they reflect modern SOC trends.
CBROPS exam name change
On February 3,2026, the CBROPS exam name and acronym will change to Understanding Cisco Cybersecurity Operations Fundamentals (CCNACBR). No changes to exam topics.
Conclusion: Make CBROPS 200-201 Your Launchpad into Cybersecurity
The CBROPS 200-201 exam is not just about passing a test—it’s about building analytical thinking, investigative skills, and SOC-ready expertise.
With the right plan, consistent practice, and reliable resources like Leads4Pass 200-201 Practice Questions (https://www.leads4pass.com/200-201.html), you can pass the exam confidently and unlock exciting cybersecurity career opportunities in 2025.